Volatility Framework | Mounting BitLocker Protected Volume
The integration of strong encryption into operating systems is creating challenges for forensic examiners, potentially preventing them from recovering any digital evidence from a computer. Because strong encryption cannot be circumvented without a key or passphrase, forensic examiners may not be able to access data after a computer is shut down
BitLocker drive encryption
 |
BitLocker is a security feature added in Windows Vista (also available in any higher version) that protects a computer's file system. BitLocker encrypts disk drives and their contents. When encrypted, others cannot see your files even if the computer had been stolen or the hard disk was taken. BitLocker also works on removable storage drives. In order to access an encrypted drive, users must authenticate/login to access the data.
Recovering the BitLocker Keys on Windows 8.1 and Windows 10 becomes crucial in order to carry on the investigation.This can be achieved using the following volatility plugin:
volatility-bitlocker
A plugin for the Volatility Framework which aims to extract BitLocker Full Volume Encryption Keys (FVEK) from memory. Works on Windows 7 through to Windows 10.
Once the key is recovered the libbde library can be used to mount BitLocker protected volumes in Linux using the FVEK and TWEAK data.
1) Key Recovery using volatility-bitlocker :
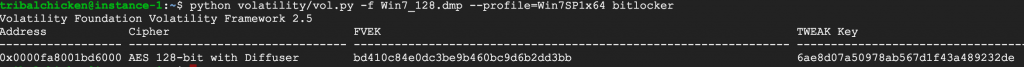
Example of a Windows 7 image:
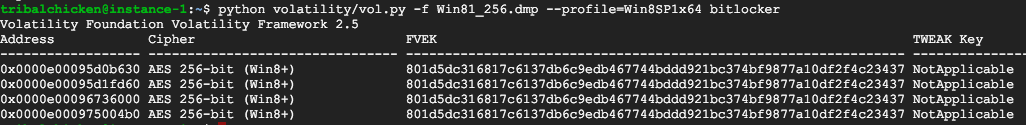
Example of a Windows 8.1 Image:
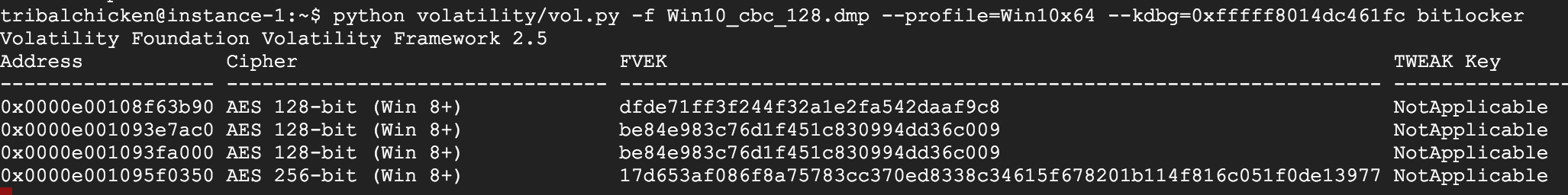
Example of a Windows 10 image (CBC):
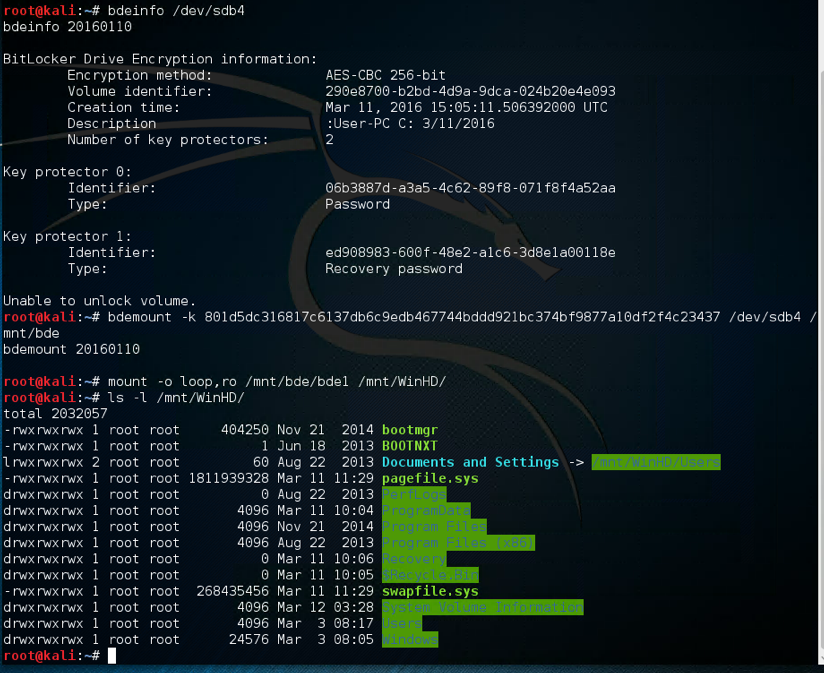
2) Mounting the protected volume (Windows 8.1 Image of above screenshot) using the FVEK data with the help of libbde library in linux:
Image Credits : tribalchicken



Comments
Post a Comment