$Recycle.Bin Forensics: Analysis of $I (metadata file) and $R (actual content)
Forensic Insight into Windows 10 $Recycle.Bin
- $I – Contains metadata specific to the deleted file (original file name path, file size, deletion timestamp, file name size and, file name).
- $R – Contains the actual contents of the file.
Let’s have an example :
Step 1 :
Below there are 2 files , a .pdf & .jpg file. We are going to delete both these files and again delete these files from the recycle bin also, since we need to recover these files.
Step 2 :
Now open the command prompt and run as administrator.
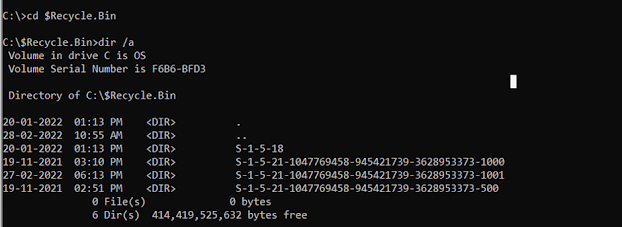
To view the hidden files type dir /a and then we can see the $Recycle.Bin
folder on the second line.
Step 3 :
Now change the directory to $Recycle.Bin by typing “cd $Recycle.Bin” and
to see files under the Recycle Bin directory type “dir /a”. The SID folders are illustrated below.
Step 4 :
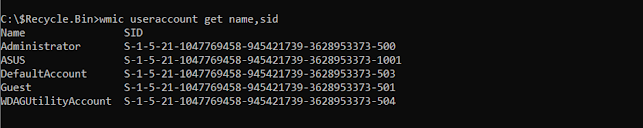
In order to determine the SID's username and other associated SID’s the following command can be used:
wmic useraccount get name,sid
Step 5 :
Let’s get into the SID folder by entering the below command:
cd S-1-5-21-1047769458-955421739-3628953373-1001
Step 6 :
Now we can copy the $R and $I file to a recovery folder by using copy
command as show below:
Syntax : copy “$R file name” “ recovery folder location”
copy “$I file name” “ recovery folder location”
Now we can see that the $I and $R files are recovered/copied in the RecoveryData
folder.
Step 7 :
The following custom developed python code may be used to recover the meta data of the files that were deleted i.e., $I file. The $I file hold the following data structure, which can be followed for the extraction of such crucial information.
import datetime
fileobj =
open("C:\\Users\\ASUS\\OneDrive\\Desktop\\RecoveryData\\$I4ARIVC.jpg","rb")
data=fileobj.read()
print(data)
def FromFileTime(filetime):
if
filetime<0:
return None
timestamp = filetime / 10
time1=datetime.timedelta(microseconds=timestamp)
date_time = datetime.datetime(1601,1,1) + time1
date_time=date_time+datetime.timedelta(minutes=330)
return date_time.strftime('%d %b %Y %I:%M:%S%p')
header = struct.unpack("<Q",data[0:8])
print(header[0]) #Header (8 Bytes)
filesize =
struct.unpack("<Q",data[8:16])
print(filesize[0]) #File size (8 Bytes)
deletion_time = struct.unpack("<Q",data[16:24])
# Time (8-Bytes)
#print(deletion_time)
print("File Deletion Date And Time=
",FromFileTime(deletion_time[0]))
name_length = struct.unpack("<L",data[24:28])
print(name_length[0]) # Filename Length or
Length of the Filename (4 Bytes)
filename = data[28:28+2*name_length[0]].decode('utf-16')
print(filename) # Filename. The size is
variable
So now we recovered the file both the Actual contents and the Meta data of
the file.
Hence these were few simple steps that can be used to recover the deleted files
from a $Recycle.Bin.








Comments
Post a Comment